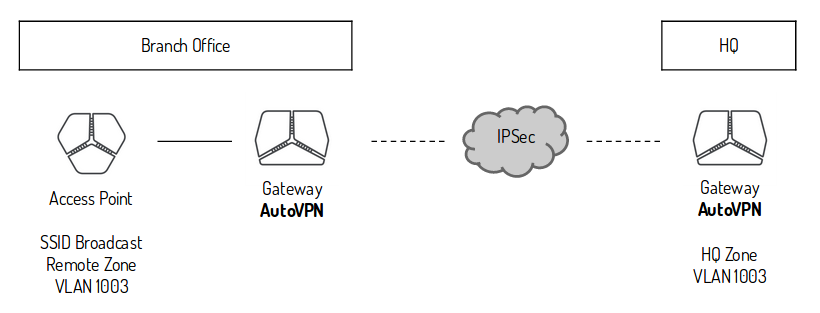
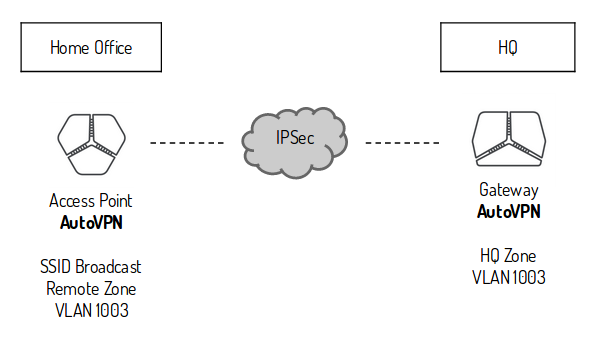
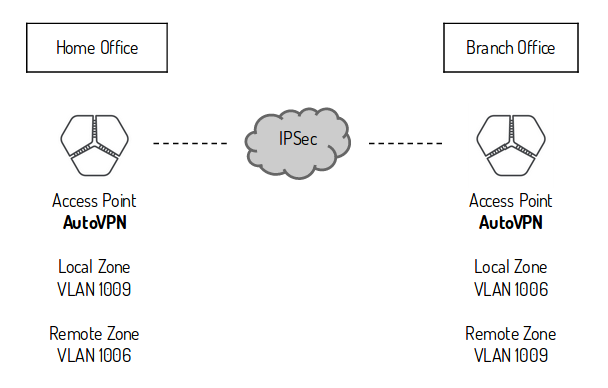
The AutoVPN feature provides connectivity between riverbed sites. In each site there can be only one appliance acting as an AutoVPN endpoint. The selected appliance should ideally be the network gateway for the site or be placed inline to pass all traffic entering and exiting the Site. On sites without a riverbed gateway you might want to enable AutoVPN for the Access Point to join the full mesh VPN network. The AutoVPN connections use AES256-SHA1 encryption and IKEv2 where NAT traversal is always being active.
AutoVPN can be split into two general operating modes:
RouteVPN – a classic routed Layer 3 IPSec VPN between internal networks
SwitchVPN – a bridged Layer 2 IPSec VPN between sites (this extends Zones across sites boundaries as needed)
AutoVPN is unlikely to work from behind NATing devices without any incoming port forwarding to AutoVPN appliance
UDP encapsulation is per default enforced on Port 4500 (source and destination port). If necessary it is also possible to change the default AutoVPN port in SteelConnect > Sites > WAN/AutoVPN > AutoVPN Port.
To make sure AutoVPN is working properly behind a NAT device, you should configure port forwarding rule on the NAT device for the AutoVPN port to forward traffic to the AutoVPN appliance, as well as check that the NAT device does not try to terminate the IPSEC tunnel (commonly reffered to as "IPSEC Passthrough")